 ...240 years ago. Amazing! Watch this short video (4:48) to learn more about it. http://www.chonday.com/Videos/the-writer-automaton
0 Comments
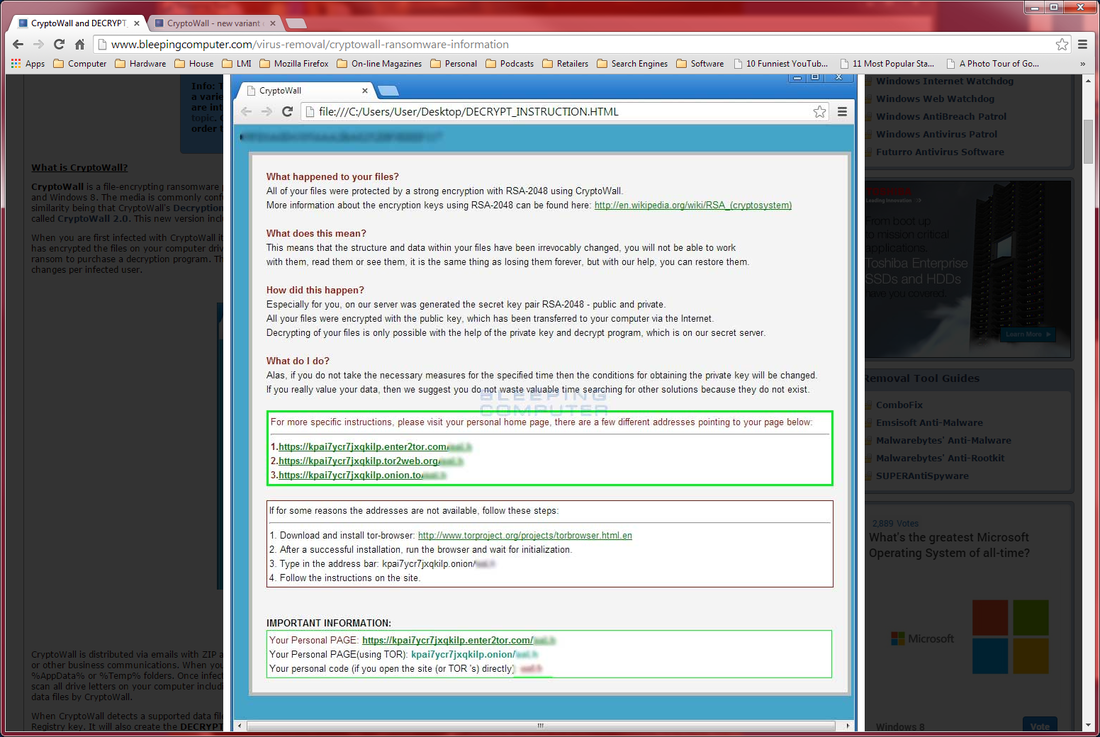
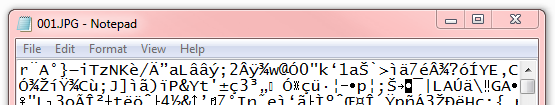
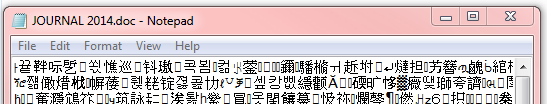
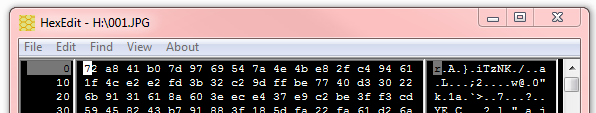
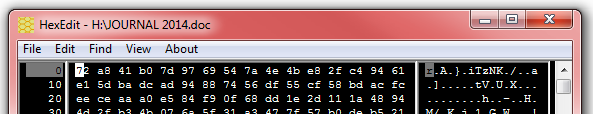
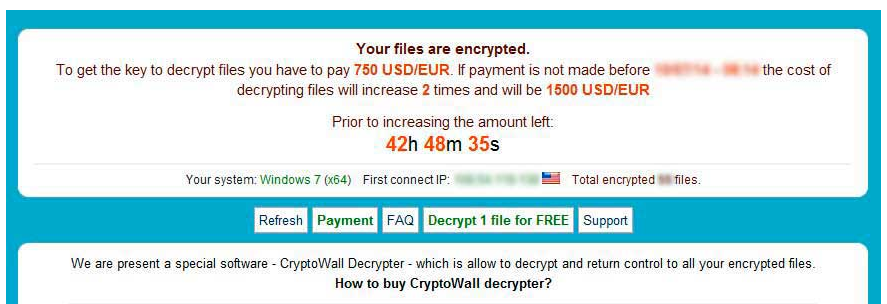
By Bob Bloom In retrospect, had I known what I know now, I might have done this differently. On the other hand, it is unlikely that the end result would be different. So, as my bosses used to say … “Bottom line up front!” BLUF: All of {the computer club member’s} data files have been encrypted by the CryptoWall computer virus. Specifically, this was all files with a DOC, DOCX, JPG, XLS, PDF, or MP3 extension, and probably more. There is no way to decrypt these files without the encryption key. CrytoWall is considered “Ransomware” as it is holding the files for ransom. One can pay the crooks their ransom and get the encryption key, but that is not recommended as it just encourages them. Instead, consider this as if the hard disk just crashed and lost all your data. Hopefully our advice about a good backup has been followed and the data files can be recovered from that. Now the details: Detailed information about the CryptoWall virus can be found here: http://www.bleepingcomputer.com/virus-removal/cryptowall-ransomware-information ) The initial symptom of this virus is an inability to open a data file, usually with an error such as “Program X can’t open data file Y because it is either corrupted or of the wrong format.” One may also have gotten a pop-up from the virus saying, in effect, “Pay up if you want your files back!” but by the time that message occurs, the damage has been done. Here is an example from Bleeping Computer: The identity of the crook is obscured by the use of TOR (“The Onion Router.”) TOR “is designed to make it possible for users to surf the Internet anonymously, so their activities and location cannot be discovered by government agencies, corporations, or anyone else.” http://en.wikipedia.org/wiki/Tor_(anonymity_network) It appears that all of the encrypted files begin with the same 16 bytes. If opened with Notepad, an encrypted file looks like this: Or this: (The above was read as ‘UNICODE’ instead of ANSI. The actual bytes are the same.) An alternate way of examining files is a hex editor. When opened in HexEdit, the two files above look like this: And Note again the first 16 bytes of the encrypted files are the same. They are, in Hex: 72 a8 41 b0 7d 97 69 54 7a 4e 4b e8 2f c4 94 61” or in ASCII, r¨A°}—iTzNKè/Ä”a”. Supposition: Those 16 bytes is the ‘signature’ for your encryption key. The crook can compare those bytes with his records to obtain the correct decryption key. All CryptoWall infections use a different, random key. Unfortunately, in this case this is encryption done right – I doubt even the NSA can break this encryption. Program files seem to be unaffected, only when a program tries to open an encrypted file does errors occur. Before we had fully understood what was happening, we had run a number of anti-virus and anti-spyware programs on your computer. These actions deleted the actual Cryptowall virus and other potentially unwanted programs (PUPs). Multiple cleanings deleted most of the Cryptowall evidence, including a list of all the encrypted files. One critical piece of evidence was originally deleted, but recovered with an undelete program: multiple copies of the file INSTALL_TOR.URL were placed in every folder that held encrypted files. This INSTALL_TOR.URL file was an Internet link to https:// paytordmbdekmizq. tor4pay. com/1egcLN6. (the link has been changed above so that it is not active.) The ‘dmbdekmizq’ is an unique identifier to the crook for this infection. Going to that site displays this: Note the button “Decrypt 1 file for FREE” – I used this to decrypt {the one file that the member really missed.} I’m sure this also kicked off the timer that increases the ransom over time; it starts at $500 and goes up to over $1,500.
Shouldn’t the Anti-virus program have stopped this? Short answer, yes. However, AV programs can never catch everything, new viruses and so-called Zero-day vulnerabilities are a constant challenge. One’s own behavior is the first line of defense. Most likely this was a new virus file that the daily updates of your AV had not yet identified. How did I get infected? I cannot definitively say. Because this infection was not immediately identified as such much of the forensic evidence has been lost. This is usual as we are normally much more interested in fixing the problem rather than determining the source. That said, Bleeping Computer indicates “CryptoWall is distributed via emails with ZIP attachments that contain executables that are disguised as PDF files.” The victim receives the email, opens the attachment which appears to hold a PDF file, e.g., the enclosed file has an Adobe Reader icon. However, the file is instead a program (executable) file which runs when the user attempts to open it. Unfortunately, the default setting of Microsoft Windows is to hide the file extension which shows the file type. Thus, a filename of “Receipt.pdf.exe,” an executable file, appears as “Receipt .pdf,” a portable document format, i.e. Adobe Reader, file. Alternately, it may be possible an infected advertisement on an otherwise innocent webpage was clicked. Per PC World, “{It} checks if users are running an unpatched version of Flash, Java or Silverlight. If someone’s computer isn’t patched {or updated}, ‘you’re instantly exploited.’” And lastly, the tried-and-true Trojan horse method has also been observed with CryptoWall. ”All the anti-malware software in the world can't protect you from yourself if you're intent on bypassing them to see the dancing bunnies you've been promised.” http://askleo.com/resist-dancing-bunnies/ Once the virus file is opened or program run, it starts searching for and encrypting data files. No message from the virus is shown. If the user has turned off the User Access Control warning, or simply clicks <yes> to the Windows warning, there are no further messages displayed. It is not until all of the files are encrypted does the virus demand money. Can’t they track the crook down through the money transfer? No. The crook wants to be paid in BitCoin. BitCoin, like cash, has been designed to be effectively non-traceable. Legal actions: There seems to be no recourse. {Our member} has joined over a million other users in losing data. There is a prevention program specifically designed to stop Cryptolocker and other similar programs called CryptoPrevent. That blocks programs from executing from commonly exploited folders. Unfortunately, all a virus has to do to avoid being blocked is to execute from a NON-common location. The authorities are pursuing the crooks. An earlier ransom ware program, CryptoLocker, has been taken down and decryption keys are available for free. For that reason I recommend not deleting encrypted files; instead move them to some folder in case CryptoWall is likewise taken down. It’s not a sure thing, and may not happen at all, but disk space is plentiful. References http://www.pcworld.com/article/2600543/cryptowall-held-over-halfamillion-computers-hostage-encrypted-5-billion-files.html http://www.pcworld.com/article/2360820/malicious-advertisements-on-major-websites-lead-to-ransomware.html http://www.theregister.co.uk/2014/10/23/cryptowall_malvertising_outbreak/ http://www.techrepublic.com/article/cryptowall-what-it-is-and-how-to-protect-your-systems/ |
TECH TEAMLatest Technology News will be presented here. Archives
August 2019
Categories
All
|
- HOME
-
ABOUT
- BOARD OF DIRECTORS >
- BYLAWS
- COMMITTEES
-
HISTORY
>
-
PHOTOS
>
- 2023 NOVEMBER SOCIAL
- 2023 JUNE SOCIAL
- 2022 DECEMBER GET TOGETHER
- 2022 JUNE GET TOGETHER
- 2019 SPRING SOCIAL
- 2018 SPRING SOCIAL
- 2017 WINTER SOCIAL
- 2017 SPRING SOCIAL
- 2016 WINTER SOCIAL
- 2016 SPRING SOCIAL
- 2015 WINTER SOCIAL
- 2015 SPRING SOCIAL
- 2015 NSC VOLUNTEER AWARDS
- 2014 EVENTS
- 2014 WINTER SOCIAL
- 2012 WINTER SOCIAL
- 2011 WINTER SOCIAL
- 2008 OPEN HOUSE
- 2008 WINTER SOCIAL
- 2007 WINTER SOCIAL
- 2007 SPRING SOCIAL
- 2006 EVENTS
- 2006 SPRING SOCIAL
- 2005 EVENTS
- 2005 WINTER SOCIAL
- 2004 OPEN HOUSE
- 2004 OPTIMIZATION DAY
- 2004 WINTER SOCIAL
- 2003 EVENTS
-
PHOTOS
>
- LOCATION
- MEMBER LINKS
- MEMBERSHIP
- MEMBER SPOTLIGHT >
- CALENDAR
- PRESENTATIONS
- APPLE
- VETERANS
- HELP
|
|
©2022– All Rights Reserved Newark Senior Center Technology Club Located at the Newark Senior Center 200 White Chapel Road --- Newark, DE 19713 webmaster@nscsurfers.org All references to goods and services provided by Apple® are trademarks of Apple Inc., registered in the U.S. and other countries and regions. All references to goods and services provided by Microsoft® are trademarks of the Microsoft group of companies. |
- HOME
-
ABOUT
- BOARD OF DIRECTORS >
- BYLAWS
- COMMITTEES
-
HISTORY
>
-
PHOTOS
>
- 2023 NOVEMBER SOCIAL
- 2023 JUNE SOCIAL
- 2022 DECEMBER GET TOGETHER
- 2022 JUNE GET TOGETHER
- 2019 SPRING SOCIAL
- 2018 SPRING SOCIAL
- 2017 WINTER SOCIAL
- 2017 SPRING SOCIAL
- 2016 WINTER SOCIAL
- 2016 SPRING SOCIAL
- 2015 WINTER SOCIAL
- 2015 SPRING SOCIAL
- 2015 NSC VOLUNTEER AWARDS
- 2014 EVENTS
- 2014 WINTER SOCIAL
- 2012 WINTER SOCIAL
- 2011 WINTER SOCIAL
- 2008 OPEN HOUSE
- 2008 WINTER SOCIAL
- 2007 WINTER SOCIAL
- 2007 SPRING SOCIAL
- 2006 EVENTS
- 2006 SPRING SOCIAL
- 2005 EVENTS
- 2005 WINTER SOCIAL
- 2004 OPEN HOUSE
- 2004 OPTIMIZATION DAY
- 2004 WINTER SOCIAL
- 2003 EVENTS
-
PHOTOS
>
- LOCATION
- MEMBER LINKS
- MEMBERSHIP
- MEMBER SPOTLIGHT >
- CALENDAR
- PRESENTATIONS
- APPLE
- VETERANS
- HELP


 RSS Feed
RSS Feed
