|
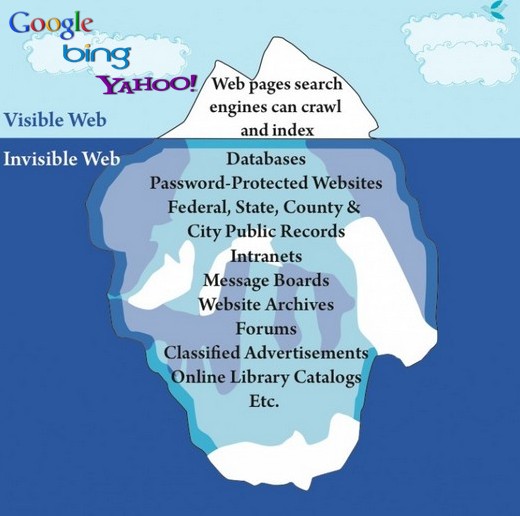
Although the “Deep Web” may be hard to understand, the concept is simple. Major search engines – Google, Yahoo, Bing – index public webpages to make it easier for you to find pages on the surface internet. The deep web is not indexed by these “visible web” search engines.
This “public” part of the internet is merely the surface of what is available on the internet. Tens of trillions, a number you cannot imagine, web pages populate the internet and most people will never see those “other” pages on the “invisible web”. They are mostly made up of boring statistics, data base information, and, of course, anything illegal you can imagine. The drawing above gives you an idea of what makes up the huge portion of the internet. But the deep web is not necessarily bad: your password protected Gmail messages live there, so do many other password protected sites. Alas, there is an underbelly of the Deep Web called the “Dark Web”. The “dark web” should never be confused with the Deep Web. You may never want to visit there, but you really should know what it is all about. Specifically, the dark web is a collection of publicly visible websites that hide their IP addresses of servers that host them. Any of these sites can be visited by any web user but you cannot find these sites using the “surface” web search engine. Almost all of the sites on the dark web use the Tor encryption tool to hide their identity. You need to use the Tor browser to take you to those places on the dark web. The browser runs on a relay system that bounces signals around to different Tor-enabled computers all over the world. Interesting in finding out more? Check out these articles: http://www.pcadvisor.co.uk/how-to/internet/3593569/what-is-dark-web-how-access-dark-web/ http://www.brightplanet.com/2014/03/clearing-confusion-deep-web-vs-dark-web/ http://www.pcmag.com/article2/0,2817,2475580,00.asp
1 Comment
bb
2/18/2015 03:07:57 am
As Yogi Berra could have put it, semantics are important, especially when dealing with words.
Reply
Your comment will be posted after it is approved.
Leave a Reply. |
TECH TEAMLatest Technology News will be presented here. Archives
August 2019
Categories
All
|
- HOME
-
ABOUT
- BOARD OF DIRECTORS >
- BYLAWS
- COMMITTEES
-
HISTORY
>
-
PHOTOS
>
- 2023 NOVEMBER SOCIAL
- 2023 JUNE SOCIAL
- 2022 DECEMBER GET TOGETHER
- 2022 JUNE GET TOGETHER
- 2019 SPRING SOCIAL
- 2018 SPRING SOCIAL
- 2017 WINTER SOCIAL
- 2017 SPRING SOCIAL
- 2016 WINTER SOCIAL
- 2016 SPRING SOCIAL
- 2015 WINTER SOCIAL
- 2015 SPRING SOCIAL
- 2015 NSC VOLUNTEER AWARDS
- 2014 EVENTS
- 2014 WINTER SOCIAL
- 2012 WINTER SOCIAL
- 2011 WINTER SOCIAL
- 2008 OPEN HOUSE
- 2008 WINTER SOCIAL
- 2007 WINTER SOCIAL
- 2007 SPRING SOCIAL
- 2006 EVENTS
- 2006 SPRING SOCIAL
- 2005 EVENTS
- 2005 WINTER SOCIAL
- 2004 OPEN HOUSE
- 2004 OPTIMIZATION DAY
- 2004 WINTER SOCIAL
- 2003 EVENTS
-
PHOTOS
>
- LOCATION
- MEMBER LINKS
- MEMBERSHIP
- MEMBER SPOTLIGHT >
- CALENDAR
- PRESENTATIONS
- APPLE
- VETERANS
- HELP
|
|
©2022– All Rights Reserved Newark Senior Center Technology Club Located at the Newark Senior Center 200 White Chapel Road --- Newark, DE 19713 [email protected] All references to goods and services provided by Apple® are trademarks of Apple Inc., registered in the U.S. and other countries and regions. All references to goods and services provided by Microsoft® are trademarks of the Microsoft group of companies. |
- HOME
-
ABOUT
- BOARD OF DIRECTORS >
- BYLAWS
- COMMITTEES
-
HISTORY
>
-
PHOTOS
>
- 2023 NOVEMBER SOCIAL
- 2023 JUNE SOCIAL
- 2022 DECEMBER GET TOGETHER
- 2022 JUNE GET TOGETHER
- 2019 SPRING SOCIAL
- 2018 SPRING SOCIAL
- 2017 WINTER SOCIAL
- 2017 SPRING SOCIAL
- 2016 WINTER SOCIAL
- 2016 SPRING SOCIAL
- 2015 WINTER SOCIAL
- 2015 SPRING SOCIAL
- 2015 NSC VOLUNTEER AWARDS
- 2014 EVENTS
- 2014 WINTER SOCIAL
- 2012 WINTER SOCIAL
- 2011 WINTER SOCIAL
- 2008 OPEN HOUSE
- 2008 WINTER SOCIAL
- 2007 WINTER SOCIAL
- 2007 SPRING SOCIAL
- 2006 EVENTS
- 2006 SPRING SOCIAL
- 2005 EVENTS
- 2005 WINTER SOCIAL
- 2004 OPEN HOUSE
- 2004 OPTIMIZATION DAY
- 2004 WINTER SOCIAL
- 2003 EVENTS
-
PHOTOS
>
- LOCATION
- MEMBER LINKS
- MEMBERSHIP
- MEMBER SPOTLIGHT >
- CALENDAR
- PRESENTATIONS
- APPLE
- VETERANS
- HELP

 RSS Feed
RSS Feed
